Jump into live projects and boost your hacking expertise.
Join live rooms, collab with hackers
and build awesome projects
Now that you are here , you are no more a beginner !
Get started with cyber security by choosing the team of your choice !






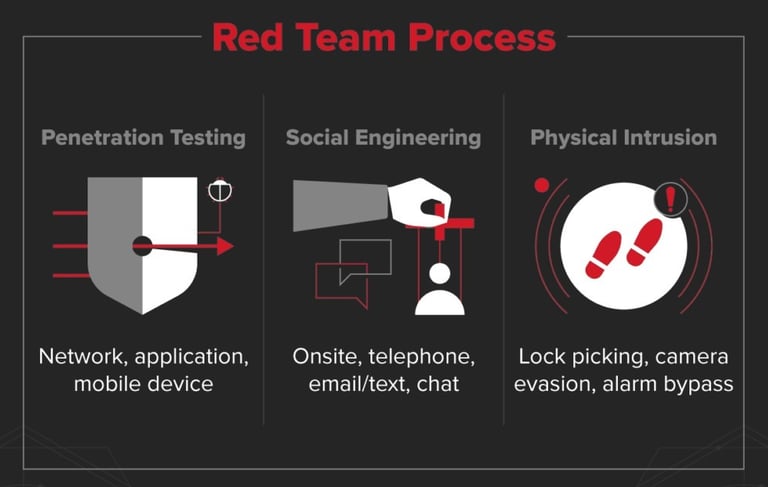
Matex Red Teaming
ThisFrom Zero to Red Team Pro — learn to attack, defend, and think like a modern adversary.
YOU’LL have hands‑on, career‑focused Red Teaming program that trains security professionals to both exploit and mitigate real‑world attacks. Learn the full cyber‑kill‑chain — reconnaissance through containment — using industry tools and live labs.
What you’ll master
Foundations: Networking, Linux, and scripting essentials every ethical hacker needs.
Recon & Discovery: Passive and active reconnaissance, scanning and enumeration with Nmap, Recon‑ng and other recon toolsets.
Web App Security: Manual and automated testing with Burp Suite, OWASP ZAP, SQLMap — identify injection, auth, logic, and configuration flaws.
Exploitation & Post‑exploitation: Metasploit, custom exploits, privilege escalation, persistence techniques and lateral movement.
Defensive Perspective: How Blue Teams detect and respond — log analysis, detection evasion tradeoffs, and containment playbooks.
Professional Skills: Clear report writing, remediation guidance, and client communication — turn findings into action.
Bug Bounty Ready: Methodologies and mindsets used by successful bounty hunters and Red Team operators.
Who this is for
Career changers and junior security pros wanting focused, job‑ready Red Team skills.
Penetration testers and bug bounty hunters looking to level up to operator‑grade techniques.
Security engineers who want the attacker’s view to improve detection and response.
Outcomes / Career path
Graduate ready for roles such as: Ethical Hacker | Penetration Tester | Red Team Operator | Bug Bounty Researcher. You’ll leave able to run end‑to‑end engagements, produce professional reports, and recommend prioritized fixes.


Matex Blue Teaming
From Zero to SOC Pro — defend, detect, and respond like a cybersecurity expert.
A hands‑on defensive security program that trains you to protect networks and systems from real-world cyber threats. Learn end-to-end SOC operations, threat detection, and incident response using industry-grade tools.
What you’ll master
Foundations: SIEM fundamentals, real-time log analysis, and network monitoring essentials.
Threat Detection: Correlate alerts, investigate anomalies, and detect threats with ELK Stack, Splunk, and Wazuh.
Frameworks & Intelligence: Understand MITRE ATT&CK, IOC identification, threat intelligence workflows, and compliance essentials (ISO 27001, SOC 2, GDPR).
System Defense: Hardening, malware analysis basics, endpoint monitoring, and risk mitigation strategies.
Incident Response: Hands-on practice responding to simulated attacks, containment, and remediation planning.
Professional Skills: Clear reporting, security documentation, and operational readiness for enterprise environments.
Who this is for
Aspiring SOC analysts, security engineers, and incident responders.
IT professionals looking to pivot into cybersecurity operations.
Students and freshers aiming for real-world defensive security experience.
Outcomes / Career path
Graduate ready for roles such as: SOC Analyst | Security Analyst | Threat Hunter | Incident Responder. You’ll gain hands-on experience monitoring, investigating, and mitigating threats in professional SOC environments.
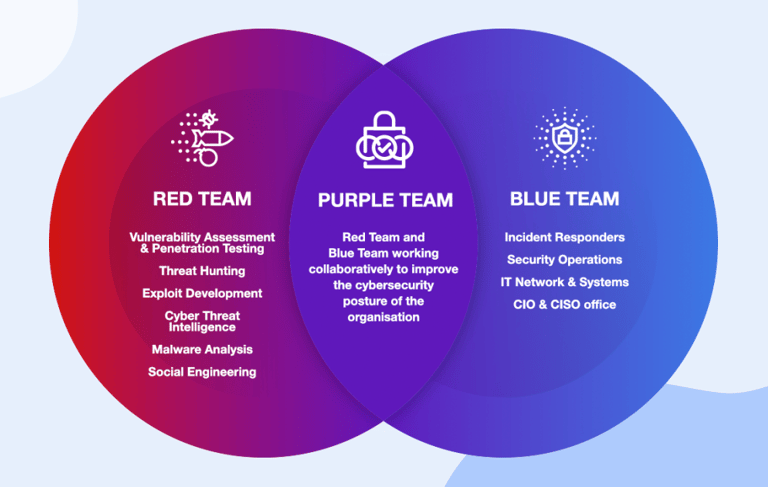
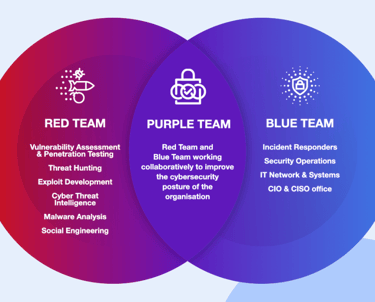
Matex Purple Teaming
Master Both Sides of Cybersecurity — Attack, Defend, and Secure Like a Pro.
An advanced, hands-on program that combines Red and Blue Team skills, training you to execute attacks, detect threats, and implement defenses in real-world enterprise environments. Understand the full cyber‑kill‑chain from compromise to containment.
What you’ll master
Red + Blue Integration: Execute offensive simulations and implement defensive countermeasures seamlessly.
Threat Emulation: Use Atomic Red Team and Caldera to simulate real-world attack scenarios.
Detection & Monitoring: Build SIEM detection rules based on Red Team activity and automate alerting.
Endpoint & Network Defense: Advanced strategies to harden systems, monitor networks, and mitigate threats.
Incident Response: Hands-on reporting, mitigation documentation, and remediation planning.
Enterprise Lab Simulations: End-to-end labs mimicking real-world organizational infrastructures for realistic practice.
Who this is for
Security professionals aiming to bridge offensive and defensive skills.
SOC leads and security engineers seeking holistic cybersecurity mastery.
Ethical hackers who want to understand defense as much as offense.
Outcomes / Career path
Graduate ready for roles such as: Purple Team Specialist | Security Engineer | SOC Lead | Cybersecurity Consultant. You’ll leave able to run full lifecycle engagements — from attack simulation to threat detection and mitigation.